- Prohibiting attacks against important networks such as med-tech facilities, healthcare institutions, manufacturing, transport/logistics or society critical infrastructure.
- Mitigating the challenge of more than 50% of cybercrimes being initiated from within a network or organisation.
- Becoming NIS 2 compliant. One of the fastest growing concerns for a huge number of organisations in Europe is to implement requirements such as authentication, encryption, secure supply chains etc.
- Allowing trusted users access to trusted critical or sensitive equipment. Any type of connection between insecure and trusted networks are by default a risk.
- Enable IT and OT networks to converge. When these two rather different networks shall communicate openly, it results in thousands of new attack vectors emerging rapidly.
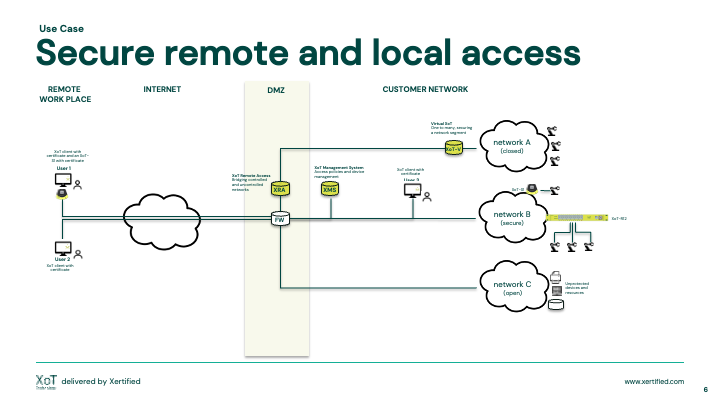
Secure remote and local access
Gain more control of who, to what and when someone or something wants to communicate.
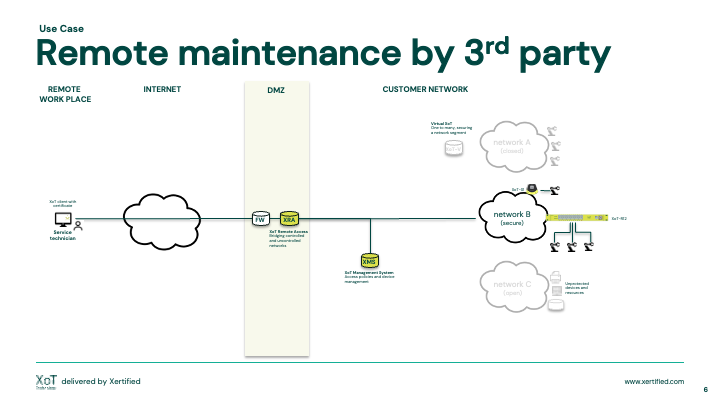
Remote maintenance by 3rd party
Secure your 3rd party supply chain maintenance.
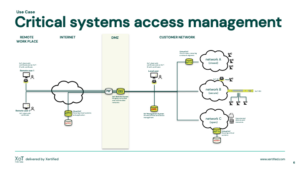
Critical systems access management
Get in access control of your system admins.
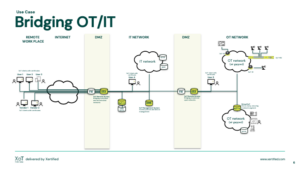
Bridging OT <-> IT
When OT meets IT, knowing who and what is on your network becomes even more critical. Only allow trusted and verified users and devices access to network resources.
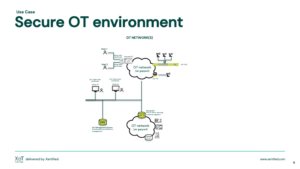
Secure OT environment
Use undeniable digital identities for man and machine.
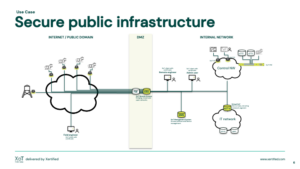
Secure public infrastructure
Dedicated secure communication beyond current VPN technologies. Dedicated device firewall with secure storage of digital identities.
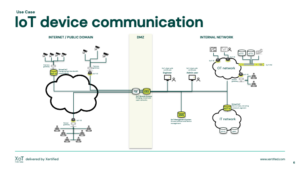
Secure IoT device communication
Ability to operate any type device over any type of network securely.
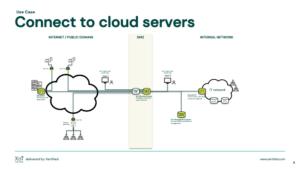
Connect to cloud servers
Secure your communication to the cloud.